I was recently reminded of the Lindy effect. It is a phenomenon whereby the longer something has been around, the longer we should expect its future life expectancy. This oddly seems to apply to Microsoft, a company that in some ways has facilitated our entire industry but is oddly in a place where they are not incentivised to build more secure products in the first place. Even when security researchers report issues, there often is no sense of urgency until Microsoft sees us, their customers, under active attack:
Microsoft Issues Patches for 121 Flaws, Including Zero-Day Under Active Attack.
This includes a DogWalk variant, which was first disclosed over 2 years ago. We are seeing patterns over and over of half-way patching, or patches introducing newer, worse problems. Microsoft’s patching is a damned-if-you-do and damned-if-you-don’t scenario, so careful management is key.
As many as 121 new security flaws were patched by Microsoft as part of its Patch Tuesday updates for the month of August, which also includes a fix for a Support Diagnostic Tool vulnerability that the company said is being actively exploited in the wild.
Of the 121 bugs, 17 are rated Critical, 102 are rated Important, one is rated Moderate, and one is rated Low in severity. Two of the issues have been listed as publicly known at the time of the release.
It’s worth noting that the 121 security flaws are in addition to 25 shortcomings the tech giant addressed in its Chromium-based Edge browser late last month and the previous week.
Read More: Microsoft Issues Patches for 121 Flaws, Including Zero-Day Under Active Attack
Open Redirect Flaws in American Express and Snapchat Exploited in Phishing Attacks.
Nearly every phishing or smishing attack involves redirection now. Even if Snapchat and American Express have closed their open redirects, nothing is preventing the criminals from using any of the thousands of other redirects. The key for protection for end users that still works here is Zero Trust connectivity.
Open redirect vulnerabilities affecting American Express and Snapchat websites were exploited earlier this year as part of phishing campaigns targeting Microsoft 365 users, email security firm Inky reports.
Open redirect flaws exist because the impacted website does not validate user input, which allows threat actors to manipulate URLs to redirect users to malicious sites.
Because the manipulated link contains a legitimate domain name, the user might consider the link safe. However, the trusted domain is only used as a landing page.
Read More: Open Redirect Flaws in American Express and Snapchat Exploited in Phishing Attacks
‘Zero Trust’ strategy is vital for cyber security.
58% of surveyed organizations are on their way to implementing Zero Trust.
Datacom Managing Director Alex Coates says ‘Zero Trust’ security practises are vital for protecting organisations.
Ms Coates said the pandemic has further exacerbated the need for ‘Zero Trust’ security practises.
“At the end of the day, Zero Trust is much more than just a technical implementation,” she told Sky News Australia.
“It’s actually a piece of organisational change, where communication is absolutely vital to its success.”
Read More: ‘Zero Trust’ strategy is vital for cyber security
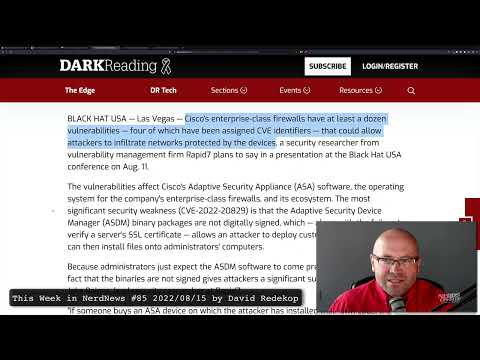
4 Flaws, Other Weaknesses Undermine Cisco ASA Firewalls.
“Cisco’s enterprise-class firewalls have at least a dozen vulnerabilities — four of which have been assigned CVE identifiers — that could allow attackers to infiltrate networks protected by the devices”
BLACK HAT USA — Las Vegas — Cisco’s enterprise-class firewalls have at least a dozen vulnerabilities — four of which have been assigned CVE identifiers — that could allow attackers to infiltrate networks protected by the devices, a security researcher from vulnerability management firm Rapid7 plans to say in a presentation at the Black Hat USA conference on Aug. 11.
The vulnerabilities affect Cisco’s Adaptive Security Appliance (ASA) software, the operating system for the company’s enterprise-class firewalls, and its ecosystem. The most significant security weakness (CVE-2022-20829) is that the Adaptive Security Device Manager (ASDM) binary packages are not digitally signed, which — along with the failure to verify a server’s SSL certificate — allows an attacker to deploy customized ASA binaries that can then install files onto administrators’ computers.
Because administrators just expect the ASDM software to come preinstalled on devices, the fact that the binaries are not signed gives attackers a significant supply chain attack, says Jake Baines, lead security researcher at Rapid7.
Read More: 4 Flaws, Other Weaknesses Undermine Cisco ASA Firewalls
The mechanics of a sophisticated phishing scam and how we stopped it.
An excellent write-up in how close these criminals got to compromising Cloudflare, but the hardware key turned out to be protecting them. We would argue, of course, that cloudflare-okta\.com, being a domain generated only 40 minutes before the campaign began, should itself be suspicious enough not to function on a network protected by Zero Trust connectivity. Separately, there’s no reason to allow remote tools like Anydesk or TeamViewer to be permitted unless required for specific use cases.
Yesterday, August 8, 2022, Twilio shared that they’d been compromised by a targeted phishing attack. Around the same time as Twilio was attacked, we saw an attack with very similar characteristics also targeting Cloudflare’s employees. While individual employees did fall for the phishing messages, we were able to thwart the attack through our own use of Cloudflare One products, and physical security keys issued to every employee that are required to access all our applications.
We have confirmed that no Cloudflare systems were compromised. Our Cloudforce One threat intelligence team was able to perform additional analysis to further dissect the mechanism of the attack and gather critical evidence to assist in tracking down the attacker.
This was a sophisticated attack targeting employees and systems in such a way that we believe most organizations would be likely to be breached. Given that the attacker is targeting multiple organizations, we wanted to share here a rundown of exactly what we saw in order to help other companies recognize and mitigate this attack.
Read More: The mechanics of a sophisticated phishing scam and how we stopped it
Did you know?
Canada’s 1st codebreaking unit comes out of the shadows. “No one outside knew what we were doing” says the 101-year-old Sylvia Gellman. “You were so aware of it being a secret mission. And you didn’t tell anybody. And I followed that very closely. I didn’t even tell my family.” Now that’s a humble servant spirit we need more of.












