Your weekly top 5 technical and security issues Nerds should pay attention to:
Article Contents
First thing’s first, at the start of this year, WTH NerdNews is renamed to TWINN for This Week In Nerd News. The focus is still in 5 mins or less to get up to speed with the most important stories and events of the week to help with our focus.
Backdoor account discovered in more than 100,000 Zyxel firewalls, VPN gateways.
It doesn’t help that ISPs commonly use Zyxel as their CPE (Customer Premise Equipment). If this is you or a client, you know what to do 🙂
More than 100,000 Zyxel firewalls, VPN gateways, and access point controllers contain a hardcoded admin-level backdoor account that can grant attackers root access to devices via either the SSH interface or the web administration panel.
Read More: Backdoor account discovered in more than 100,000 Zyxel firewalls, VPN gateways
Forbes Cybersecurity Awards 2020: Corellium, The Tiny Startup Driving Apple Crazy.
With a significant court victory in December, this is good news for security researchers and our industry.
The end of the year in cybersecurity mirrored the wider world by concluding in catastrophe: With more than 10,000 people dying every day from Covid-19, a highly sophisticated electronic espionage campaign targeted U.S. government agencies and critical private industry, all customers of a single company: SolarWinds.
Read More: Forbes Cybersecurity Awards 2020: Corellium, The Tiny Startup Driving Apple Crazy
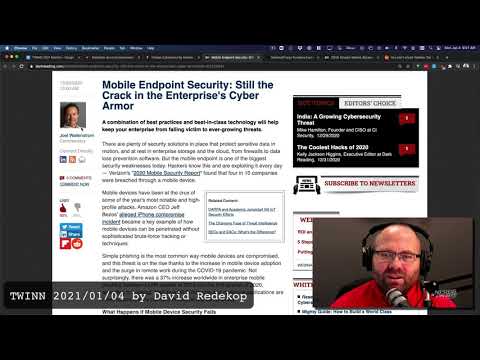
Mobile Endpoint Security: Still the Crack in the Enterprise’s Cyber Armor.
This is consistent with what we’ve been communicating over the last few years, which is why adam:GO exists in the first place.
There are plenty of security solutions in place that protect sensitive data in motion, and at rest in enterprise storage and the cloud, from firewalls to data loss prevention software. But the mobile endpoint is one of the biggest security weaknesses today. Hackers know this and are exploiting it every day — Verizon’s “2020 Mobile Security Report” found that four in 10 companies were breached through a mobile device.
Read More: Mobile Endpoint Security: Still the Crack in the Enterprise’s Cyber Armor
Microsoft says Russians hacked its network, viewing source code.
Just viewing the source code itself, in this case, can lead to future stealth hacks even more advanced than Solarigate.
Russian government hackers engaged in a sweeping series of breaches of government and private-sector networks have been able to penetrate deeper into Microsoft’s systems than previously known, gaining access to potentially valuable source code, the tech giant said Thursday.
Read More: Microsoft says Russians hacked its network, viewing source code
DDoS Attacks Spiked, Became More Complex in 2020.
Not surprising.
The large-scale shift to remote work and the increased reliance on online services as the result of the global pandemic this year gave threat actors new opportunities to use distributed denial-of-service (DDoS) attacks to harass and extort organizations.
Did you know?
TedLexa is a demonstration of an actual teddy bear, voice animated by an Arduino and Raspberry Pi to make mouth/eye movements in real-time to any sound flowing through it.